Configuring Remote Access VPN on Firepower
In this article we are going to take a look at how to configure remote access VPN's on Firepower devices.
This demonstration is based on the following lab environment:
- Cisco Virtual Firepower Management Center
- Cisco Virtual Firepower Threat Defense
- Cisco ISE 2.6
- Windows host with AnyConnect VPN
- Windows Server 2019 (CA Server)
All Firepower devices are running version 6.5
Note: ISE is used for authentication and authorization in the following lab however the configuration elements of ISE are out of scope for this demonstration.
Generate a CSR for Remote Access VPN's
Those accessing your network remotely need to trust the service you're running. Without the correct trust users could face issues connecting via VPN.
With access to the FMC navigate to Objects > Object Management > PKI > Cert Enrollment
Assuming you are opting for manual enrollment, select 'Manual' in Enrollment Type and copy the CA Certificate BASE-64 into the field.
Now select the 'Certificate Parameters' tab and select 'Custom FQDN'. We will use a separate FQDN for remote access VPN services. It is also worth making sure the FQDN is added to your internal DNS.
Continue to populate the remaining fields with the relevant information necessary to your organization.


On the 'Key' tab give the RSA key a name and specify the key length. Decide whether you would like to enable advanced options and certificate revocation checks. For the purpose of this demonstration, we will not enable advanced key features or use revocation checks.


Once done, click 'Save'.
Navigate to Devices > Certificates and click 'Add' to add a new certificate. When the pop-up box appears, select the relevant FTD appliance followed by the cert enrollment that was previously created.
Click 'Ok' when done.


Once configured, click 'ID' to generate the CSR. Copy the CSR to the CA and have it signed.
Once the certificate has been signed by your CA, download the newly signed certificate and import it to the FMC by clicking 'Import'.


Configure RADIUS Servers
Navigate to Objects > RADIUS Server Group and add a new RADIUS server group.


Configure VPN Address Pools
Navigate to Objects > Object Management > Address Pools and create your VPN address pools.
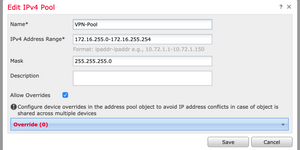

You have the option to modify the AnyConnect profile and add the new VPN FQDN if you wish. For the purpose of this demonstration we won't be going through those steps.
Upload Cisco AnyConnect Images
Upload the relevant AnyConnect images to the FMC by navigating to Objects > Object Management > VPN > AnyConnect File.


Configuring the Remote Access VPN
Navigate to Devices > VPN > Remote Access and click 'Add'.


A wizard will appear where you will run through 5 steps.
Starting with Step 1, populate the fields with the relevant settings required for your deployment. Ensure that you select the correct managed device based on where the VPN is to be deployed and select the the VPN protocols you wish to use. For the purpose of this lab, the default VPN protocol settings will be applied.
Once you are happy with the settings, proceed to step 2.


Step 2 focuses on configuration of connection profiles.
Proceed to populate the AAA fields with the objects created earlier followed by the selection of the VPN Pool you created earlier in this article.
Before moving along to step 3, you may want to edit the default group policy settings or create a new one. For the purpose of this lab, the default group policy has been modified to include split-tunneling options and DNS Servers.
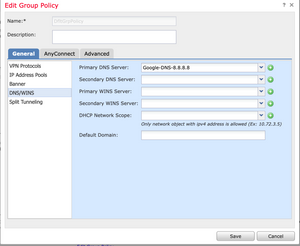

Proceeding to Step 3, you will be required to select the AnyConnect images you want to be enabled.
If no images exist you will be required to upload at least one before proceeding to Step 4.


In step 4 you are required to select the VPN termination interface as well as the certificate that should be used. You can optionally choose to bypass the ACP applied to the managed device for VPN connections. In this demonstration, we will bypass the ACP and applied access controls once users have been authorized by ISE.


Once you are happy with the settings applied in Step 4, the configuration for Remote Access VPN is complete. Proceed to Step 5 and verify the configuration settings that will be applied.


Return to Devices > VPN > Remote Access and click on the 'Access Interfaces' tab. Verify the interface and port settings.
Additional Configuration
Depending on your setup, you may need to configure additional settings such as NAT. In the lab used in this demonstration NAT is enabled on the Firepower device so the following NAT rule is to be configured.
Source interface: Any
Destination interface: Any
Original Source: Any (or specific public IPs)
Original Destination: Any
Translated Source: VPN Pool
Translated Destination: VPN Pool
No proxy-arp: enabled


If using ISE to provide policy decisions, ensure that the managed device is configured as a NAD in ISE and ensure that your policies are configured correctly.
In this demonstration, ISE is used for Authentication and Authorization of VPN clients.


You should now be able to connect to to your managed device using your AnyConnect client.
