Remote Access VPN Authentication with Cisco ISE
In this article I will walk through the steps that are required to configure the ASA for external authentication using Cisco ISE for remote access VPN users.
This demonstration will use the following devices:
- Cisco ISE 2.4
- Cisco ASA 9.8
- Cisco AnyConnect 4.6
- Test Laptop
- Server 2012 R2
Overview
Cisco ISE can be used to authenticate remote access users terminating on a Cisco ASA. Before users gain access to the network, they are required to authenticate using a set of credentials, often certificate-based or by using a username and password. Based on the user authentication, Cisco ISE can be used to determine which tunnel-group the user should be placed within.
Change of Authorization (CoA) is supported from ASA version 9.2.1, this allows for ISE to perform things such as posturing. Although not the main focus of this article, Cisco ISE can also be used to apply things such as Dynamic Access Control Lists (dACL’s) based on matched authorization policies.
Demonstration Topology
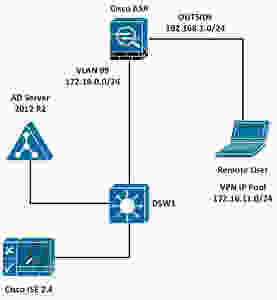

In this demonstration we will take a look at how to configure the Cisco ASA so that Remote-Access (RA) users can access the corporate network. We will also take a brief look at the authentication and authorization policies within ISE. Server 2012 configuration is beyond the scope of this demonstration and will not be shown however may be used.
The topology presented above will be used for this demonstration. Below is an overview of what happens when a remote user attempts to authenticate onto the network.
- The remote user initiates the connection to the network using the Cisco Anyconnect VPN module.
- The RADIUS access-request for the user is sent from the ASA to Cisco ISE.
- The username and password is checked against Active Directory and provided that the credentials are correct and the relevant policies within ISE are matched, the user is granted access.
The following configuration relates to the topology used for this demonstration. Depending on your environment, the configuration might be different.
ASA Configuration
Download AnyConnect Client Package
In the first step, you are required to download the Cisco Anyconnect Client Package from software.cisco.com. This is required so that the AnyConnect client can be downloaded first attempts to the ASA.
The packages vary depending on operating system. You can download Windows, MAC and Linux packages. The packages are stored within the ASA’s flash and providing you have more than one operating system that is required to authenticate, it is worth ordering the packages. The best practice is to order the packages based on the most used operating system.
To order the packages you first need to enable the remote access VPN.
Configure ISE RADIUS Servers
Configure the ASA with ISE as the AAA server. This demonstration uses a single IP address for Cisco ISE.
ASA(config)# aaa-server ISE protocol radius ASA(config-aaa-server-group)# aaa-server ISE (dmz-mgmt) host 172.16.0.254 key <omitted>
Enable Remote Access VPN
To enable remote access VPN on the ASA’s outside interface, enter the following configuration.
ASA(config)# webvpn ASA(config-webvpn)# enable outside
Specify Order of AnyConnect Client Packages
If you have more than one client package you can specify the relevant order by entering the following configuration and enable AnyConnect.
ASA(config-webvpn)# anyconnect image flash:/anyconnect-win-4.6.02074-webdeploy-k9.pkg 1 ASA(config-webvpn)# anyconnect enable
Create a VPN IP Pool
Create an IP pool that will be used for RA VPN users. This lab uses a range of IP addresses within the 172.16.11.0/24 subnet. No mask has been specified however one can be specified if required.
ASA(config)# ip local pool VPN_POOL 172.16.11.50-172.16.11.60
Create a Tunnel Group
When using ISE to authenticate VPN users, the tunnel-group used is the default tunnel-group ‘DefaultWEBVPNGroup’. We need to enter the default tunnel-group and point the ASA to authenticate using ISE.
ASA(config)# tunnel-group DefaultWEBVPNGroup general-attributes ASA(config-tunnel-general)# authentication-server-group ISE
Create a Group Policy
A group-policy is tied to a tunnel-group and specifies attributes such as DNS servers and domains that should be used among other attributes. As part of this demonstration we will configure the DNS addresses that should be used, domain name, address pools, the VPN tunneling protocol and whether traffic should be tunneled.
We will use internal attributes for the group-policy, that is attributes that are stored locally.
- DNS Servers: 8.8.8.8 and 79.79.79.79
- Tunnel-protocol: SSL-Client
- Split Tunnel Policy: Tunnel all
- Domain: wizkid.co.uk
- Address Pools: VPN_POOL
ASA(config)# group-policy VPNLAB-GP internal ASA(config)# group-policy VPNLAB-GP attributes ASA(config-group-policy)# dns-server value 8.8.8.8 79.79.79.79 ASA(config-group-policy)# vpn-tunnel-protocol ssl-client ASA(config-group-policy)# split-tunnel-policy tunnelall ASA(config-group-policy)# default-domain value wizkid.co.uk ASA(config-group-policy)# address-pools value VPN_POOL
Staying in the group policy, we want to ensure that the client remains installed on the end user machine when the session has ended. We will also configure the ASA so that AnyConnect is automatically downloaded.
ASA(config-group-policy)# webvpn ASA(config-group-webvpn)# anyconnect keep-installer installed ASA(config-group-webvpn)# anyconnect ask none default anyconnect
Access the default group policy ‘DfltGrpPolicy’ and allow the SSL client protocol.
ASA(config)# group-policy DfltGrpPolicy attributes ASA(config-group-policy)#vpn-tunnel-protocol ssl-client
Ensure NAT is in Order (Optional)
Due to the configurations and subnets used in this lab, a specific NAT rule was required to overcome an asymmetric NAT issue. This part is optional however it is worth pointing it out if you have overlapping subnets in your environment.
ASA(config)# nat (any,any) source static VPN-SUBNET VPN-SUBNET no-proxy-arp
Configure Cisco ISE
We will now move onto the configure for Cisco ISE.
Add ASA as a Network Access Device
Add the Cisco ASA as a network device on ISE. Navigate to Administration > Network Resources > Network Devices and click ‘Add’. Ensure the same RADIUS key that was configured on the ASA is also configured on Cisco ISE.


Create an Authorization Profile
We will now create an authorization profile to be used within our authorization policy. We will enable the ‘ASA VPN’ radio button and within the box we will enter the exact name of the group policy we created earlier. That name was ‘VPNLAB-GP’, all the other settings can remain the same unless your environment has additional requirements.
Navigate to Policy > Policy Elements > Results > Authorization Profiles


Create a VPN Policy Set
Navigate to Policy > Policy Sets and select the ‘+’ icon to add a new policy set for VPN authentication and authorization. As per the screenshot below, my VPN policy set is based on device types that match ‘VPN Device’ however you can choose something completely different within your condition should you choose to. Allowed protocols have been left as default for the purpose of this lab.


Within the policy set, create an authentication and an authorization policy. For the purposes of this lab, the authentication policy has been left in its default state. ‘All_User_ID_Stores’ has been configured to check the Internal User database as well as Active Directory for users attempting to authenticate onto the network. The authorization policy however has been configured with a basic condition and if that condition is met then we will apply the authorization profile ‘VPNLAB’ which was created previously. The authorization policy condition is ‘Network_Access_Authentication_Passed’ for those that are following the exact steps.


Create Users (Optional)
In this step we will create an internal user within ISE that we will use to authenticate onto the network. This step is optional depending on your environment. If your ISE deployment is bind to your active directory, then it is recommended that AD is used to authenticate users.
Navigate to Administration > Identity Management > Users
Add a new user. For the purpose of this lab, I have added a user called Kelvin and configured it with a password.


Testing & Verification
With the Cisco ASA and ISE configured, we should be in a position to test and verify that RA VPN authentication now works.
Remote User Testing
Ensuring that you have access to the remote device, open a browser and navigate to the outside IP address of the ASA. In my case the IP address is 192.168.1.2.
Open a browser and navigate to https://192.168.1.2 where you should be presented with the following screen asking for credentials.


Enter the username and password created on ISE. In my lab the username is ‘Kelvin’.
Once logged-in you should be presented with a screen that will either automatically download Cisco AnyConnect or give you the option to download it. Download Cisco Anyconnect and run the program once downloaded.

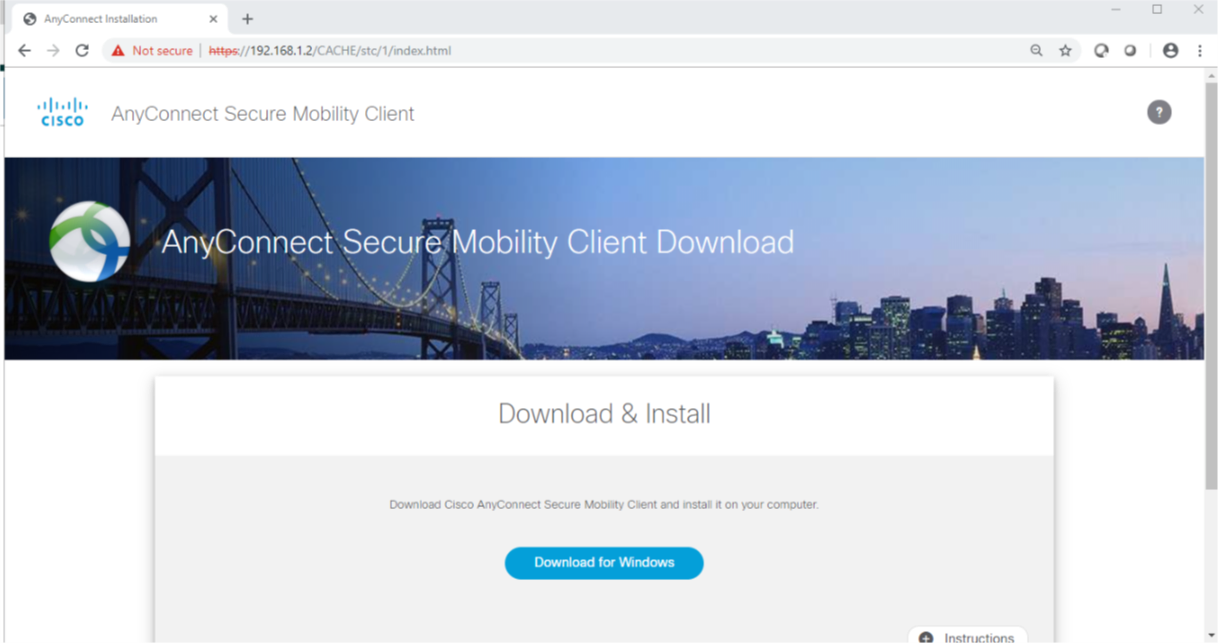


Once Cisco AnyConnect is installed, open the program and you should be presented with a box on the right-hand side of your screen. Enter the IP address of the ASA again and click ‘Connect’.


If your ASA is using untrusted certificates then you will need to change the AnyConnect settings before you can connect. Click ‘Change Settings’ and deselect the radio button ‘Block connections to untrusted servers’. Note that this is only recommended within a lab environment and trusted certificates should be used where necessary.




Save the changes and attempt to re-connect, this time your connection attempt should be successful and you should be granted network access given that your configuration is correct.






Verify your network adapter settings and IP settings.
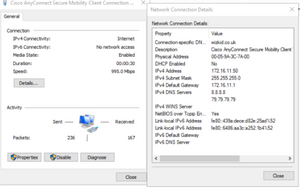

Open the Cisco AnyConnect settings and verify the IP settings. The IP settings should be the same as the adapter however you have the option to view additional security configurations.

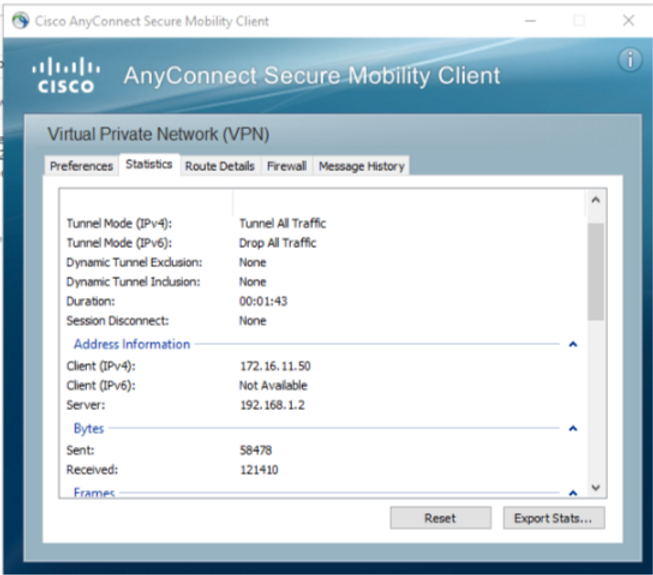
Staying on Cisco AnyConnect, browse over to the ‘Message History’ tab and view the VPN logs.


Test network access. Depending on your environment, you should be able to reach the internet as well as internal resources.


Cisco ASA Verification
Open a CLI session to the ASA. We will now take a look at the appplied configuration. Issue the command show vpn-sessiondb anyconnect. You should be able to see your connected session along with the tunnel-group and group policy applied to the user. You will also see other details such as the public IP address of the user and the IP address that was assigned by the ASA.
ASA# show vpn-sessiondb anyconnect Session Type: AnyConnect Username : administrator Index : 63411 Assigned IP : 172.16.11.50 Public IP : 192.168.1.28 Protocol : AnyConnect-Parent SSL-Tunnel DTLS-Tunnel License : AnyConnect Premium Encryption : AnyConnect-Parent: (1)none SSL-Tunnel: (1)AES-GCM-256 DTLS-Tunnel: (1)AES256 Hashing : AnyConnect-Parent: (1)none SSL-Tunnel: (1)SHA384 DTLS-Tunnel: (1)SHA1 Bytes Tx : 1030278 Bytes Rx : 3050092 Group Policy : VPNLAB-GP Tunnel Group : DefaultWEBVPNGroup Login Time : 12:25:51 UTC Sun May 26 2019 Duration : 0h:28m:02s Inactivity : 0h:00m:00s VLAN Mapping : N/A VLAN : none Audt Sess ID : 0a0000020f7b30005cea85cf Security Grp : none
You can see even more details such as the clients OS and version by entering the following command show vpn-sessiondb detail anyconnect.
KCHM5506X# show vpn-sessiondb detail anyconnect Session Type: AnyConnect Detailed Username : administrator Index : 63411 Assigned IP : 172.16.11.50 Public IP : 192.168.1.28 Protocol : AnyConnect-Parent SSL-Tunnel DTLS-Tunnel License : AnyConnect Premium Encryption : AnyConnect-Parent: (1)none SSL-Tunnel: (1)AES-GCM-256 DTLS-Tunnel: (1)AES256 Hashing : AnyConnect-Parent: (1)none SSL-Tunnel: (1)SHA384 DTLS-Tunnel: (1)SHA1 Bytes Tx : 1054605 Bytes Rx : 3081200 Pkts Tx : 5181 Pkts Rx : 6916 Pkts Tx Drop : 0 Pkts Rx Drop : 0 Group Policy : VPNLAB-GP Tunnel Group : DefaultWEBVPNGroup Login Time : 12:25:51 UTC Sun May 26 2019 Duration : 0h:31m:30s Inactivity : 0h:00m:00s VLAN Mapping : N/A VLAN : none Audt Sess ID : 0a0000020f7b30005cea85cf Security Grp : none AnyConnect-Parent Tunnels: 1 SSL-Tunnel Tunnels: 1 DTLS-Tunnel Tunnels: 1 AnyConnect-Parent: Tunnel ID : 63411.1 Public IP : 192.168.1.28 Encryption : none Hashing : none TCP Src Port : 65083 TCP Dst Port : 443 Auth Mode : userPassword Idle Time Out: 30 Minutes Idle TO Left : 0 Minutes Client OS : win Client OS Ver: 10.0.17134 Client Type : AnyConnect Client Ver : Cisco AnyConnect VPN Agent for Windows 4.6.02074 Bytes Tx : 7619 Bytes Rx : 0 Pkts Tx : 5 Pkts Rx : 0 Pkts Tx Drop : 0 Pkts Rx Drop : 0 SSL-Tunnel: Tunnel ID : 63411.2 Assigned IP : 172.16.11.50 Public IP : 192.168.1.28 Encryption : AES-GCM-256 Hashing : SHA384 Ciphersuite : ECDHE-RSA-AES256-GCM-SHA384 Encapsulation: TLSv1.2 TCP Src Port : 65086 TCP Dst Port : 443 Auth Mode : userPassword Idle Time Out: 30 Minutes Idle TO Left : 0 Minutes Client OS : Windows Client Type : SSL VPN Client Client Ver : Cisco AnyConnect VPN Agent for Windows 4.6.02074 Bytes Tx : 7619 Bytes Rx : 313 Pkts Tx : 5 Pkts Rx : 5 Pkts Tx Drop : 0 Pkts Rx Drop : 0 DTLS-Tunnel: Tunnel ID : 63411.3 Assigned IP : 172.16.11.50 Public IP : 192.168.1.28 Encryption : AES256 Hashing : SHA1 Ciphersuite : DHE-RSA-AES256-SHA Encapsulation: DTLSv1.0 UDP Src Port : 52319 UDP Dst Port : 443 Auth Mode : userPassword Idle Time Out: 30 Minutes Idle TO Left : 29 Minutes Client OS : Windows Client Type : DTLS VPN Client Client Ver : Cisco AnyConnect VPN Agent for Windows 4.6.02074 Bytes Tx : 1041452 Bytes Rx : 3083084 Pkts Tx : 5178 Pkts Rx : 6919 Pkts Tx Drop : 0 Pkts Rx Drop : 0
Cisco ISE Verification
To finish off our verification checks, we will take a look at the logs within Cisco ISE. With access to Cisco ISE, navigate to Operations > RADIUS > Live Logs. Within the live logs you should be able to see the authenticated session for the remote user. Clicking on the magnifying glass of that log you will be able to drill-down into more detail to the policies that were matched, the authentication identity store and more.


You should now have a fully working RA VPN solution that works with Cisco ISE.
